The Greatest Laptops to Run Minecraft
Introduction Some see Minecraft as the most crucial game ever released in the last ten years and see it as…
QR Code Almost Disappeared, But the Corona Pandemic Saved it
Introduction The appearance of the QR code (QR) dates back to 1994, making it obsolete compared to the product advertised:…
What is Esoszifediv Found In?
What is Esoszifediv Found In If you’ve been searching for what is esoszifediv found in, you’re not alone. Many people…
Five Simple Steps to Improve Your Job Experience
Introduction Job Experience Enhancing the job experience of an applicant for a job in the organization is one of the most…
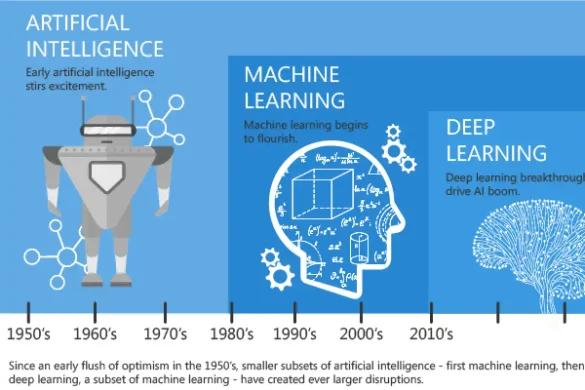
Artificial Intelligence, Machine Learning and Deep Learning?
Introduction Raise your hand if you are confused about the distinction between artificial intelligence, machine learning and deep learning. We…
Is Your Phone Spying on What You’re Saying?
Introduction Is Your Phone Spying on What You’re Saying? Have you ever talked to a friend about buying a particular…
Scientists Make Diamonds in The Lab Without Heat.
Introduction Diamonds form in nature deep in the earth and take billions of years to create, and require high-pressure environments…
Wafid Medical Status Check: How to Check Your Medical Report Online
If you’re looking for a quick and easy way to perform a wafid medical status check, you’re in the right…